If you haven't heard it before: reconnaissance is crucial to success. This is true in every area of offense. The more you know about your target, the more likely you are to succeed. In this post, I'm going to show you a few ways to gather information on a target's perimeter infrastructure using OSINT, or Open Source Intelligence. If you aren't familiar, OSINT is a method of gathering information from publicly available data to convert to actionable intelligence. That's key to understanding this entire process. You can have all the information in the world, but not knowing how to turn it into actionable intelligence makes it essentially useless.
Where to Practice
One of the most difficult things for me when I first started learning how to "hack" was finding somewhere to practice (legally). The volume of resources we have today just weren't available. Now, one of the best ways to practice perimeter penetration testing skills is by finding a company with a bug bounty program. For my examples, I'm going to choose targets on the HackerOne platform. Let's start by looking for programs with an in-scope asset of "CIDR". CIDR stands for classless inter-domain routing, and is a method of IP address allocation that improves upon the former class-full scheme. If you're still using class A/B/C, it's time to join us in the year 2024 and quit wasting network space.
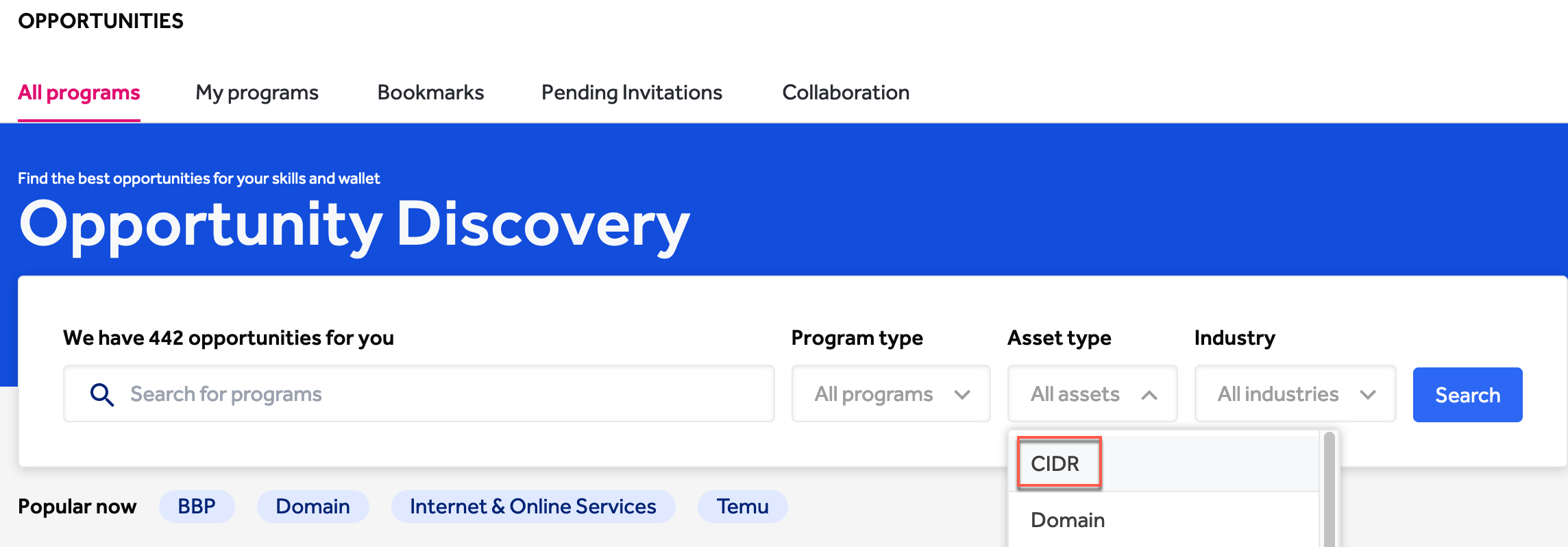
If you care about the money, you want to make sure you pay attention to which programs offer bounty, and if the CIDR range is eligible for bounty. For now, I'm going to choose something with a decent list of in-scope assets, such as the program for ForeScout Technologies.
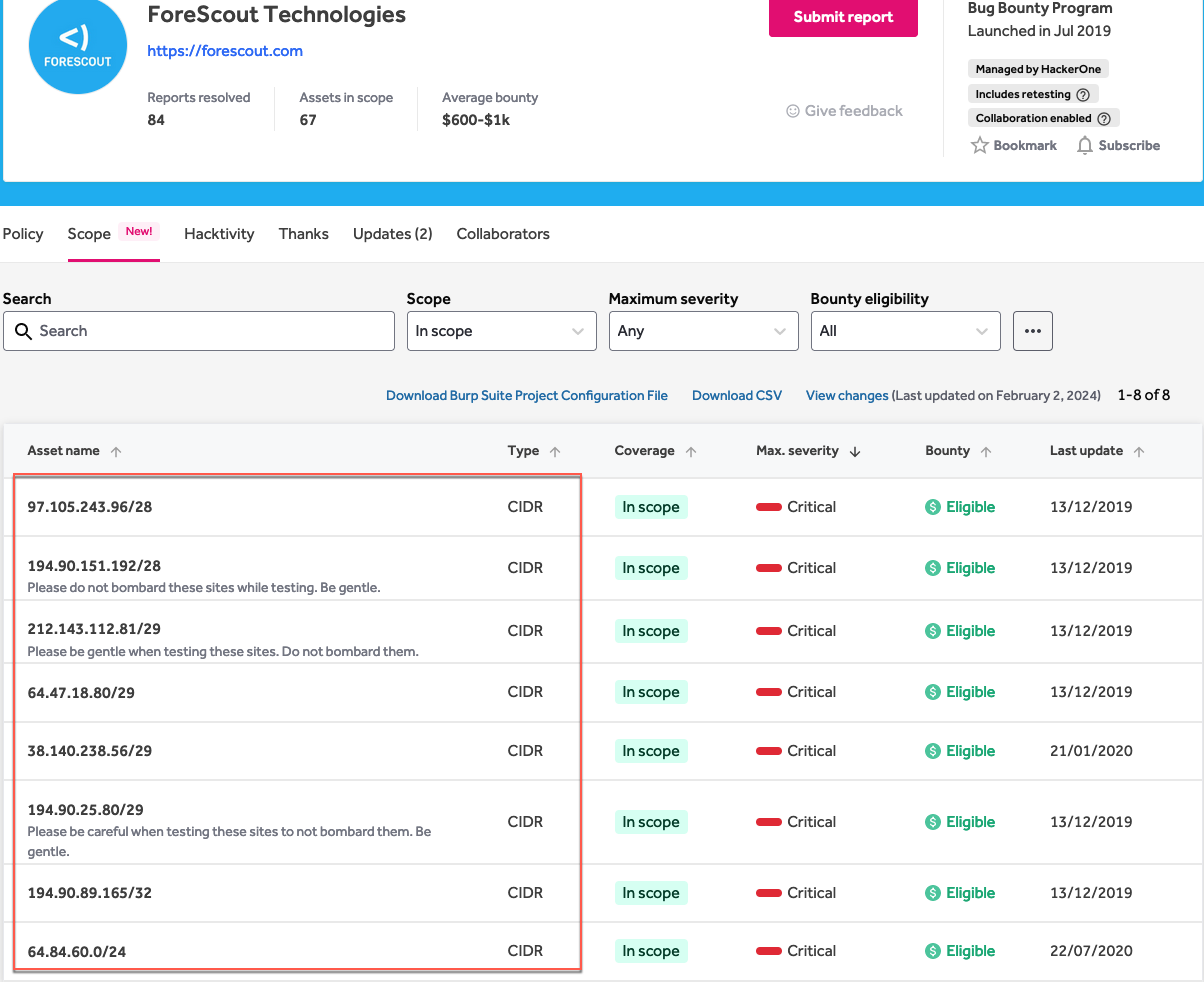
Getting Started
Now that you've got a list of ranges, it's time to start fingerprinting what's out there. A reminder, we're currently doing this (semi)passively, which means no port scanning. We will however connect to assets. Our first stop is arin.net. This is the American Registry for Internet Numbers, and holds all sorts of information about IP addresses, such as who they belong to, who to contact about them, their primary address, and their ISP. In the first listed range for ForeScout, we get most of this information.
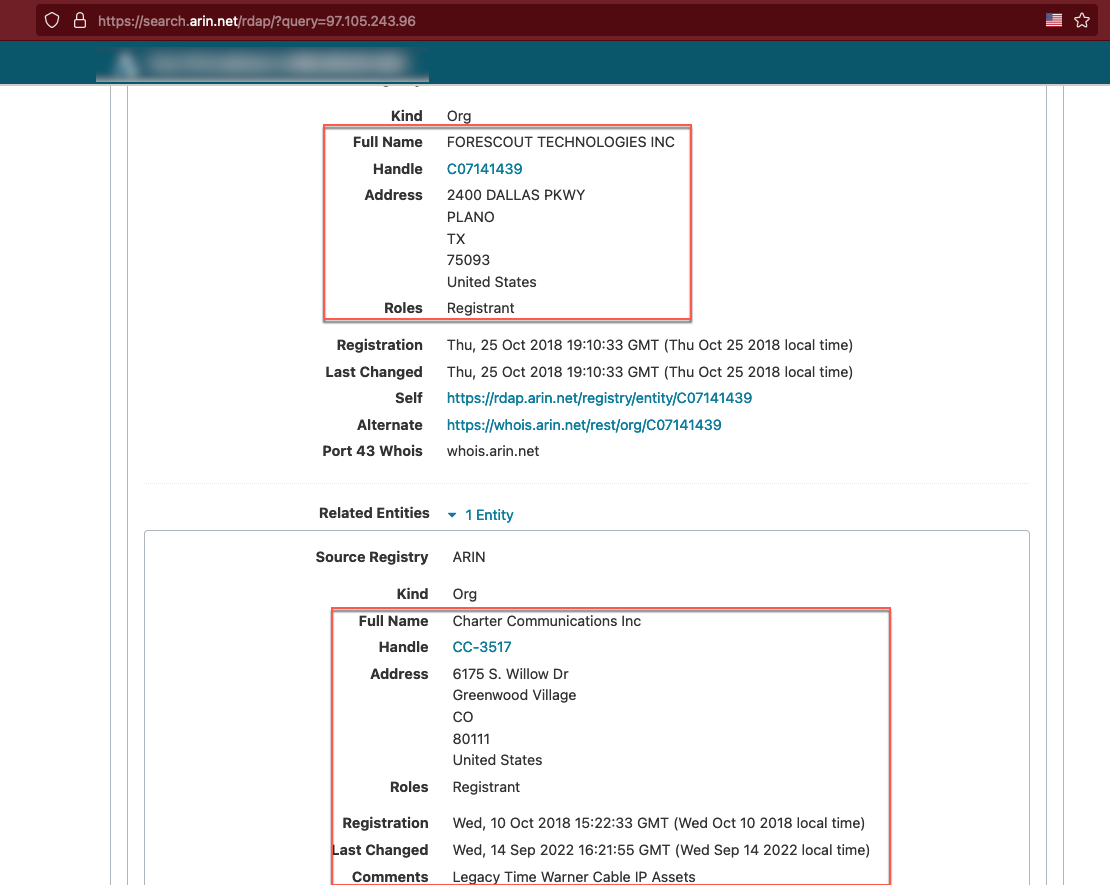
In some cases, you can even use this as a starting point if you don't have any IP addresses for a target organization. You can search the site for the name of the company, or you can use a Google dork to look for listed ranges by using site:arin.net company name here. You can also use site:ftp.arin.net company name.
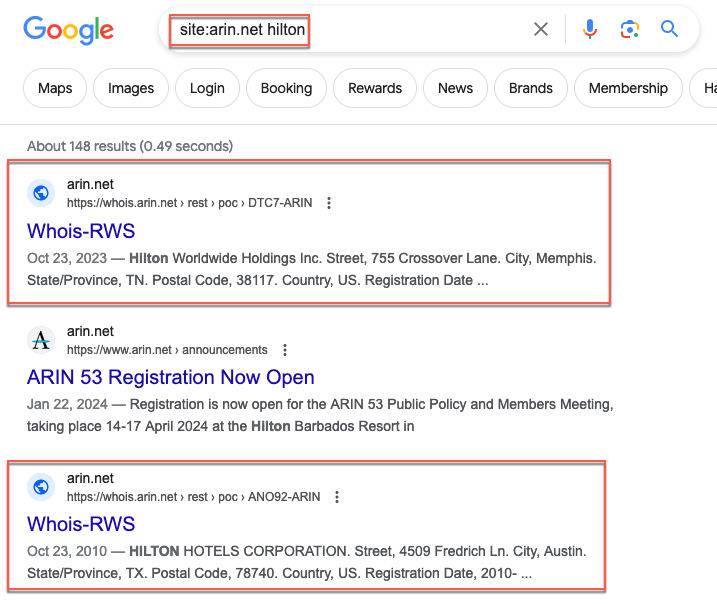
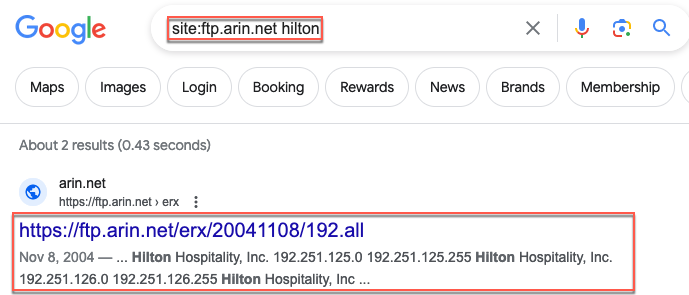
Next you'll want to do some initial reconnaissance of their domain and subdomains. We can start by performing a whois lookup. I prefer to use ICANN's site for this, but you can use whatever you like best.
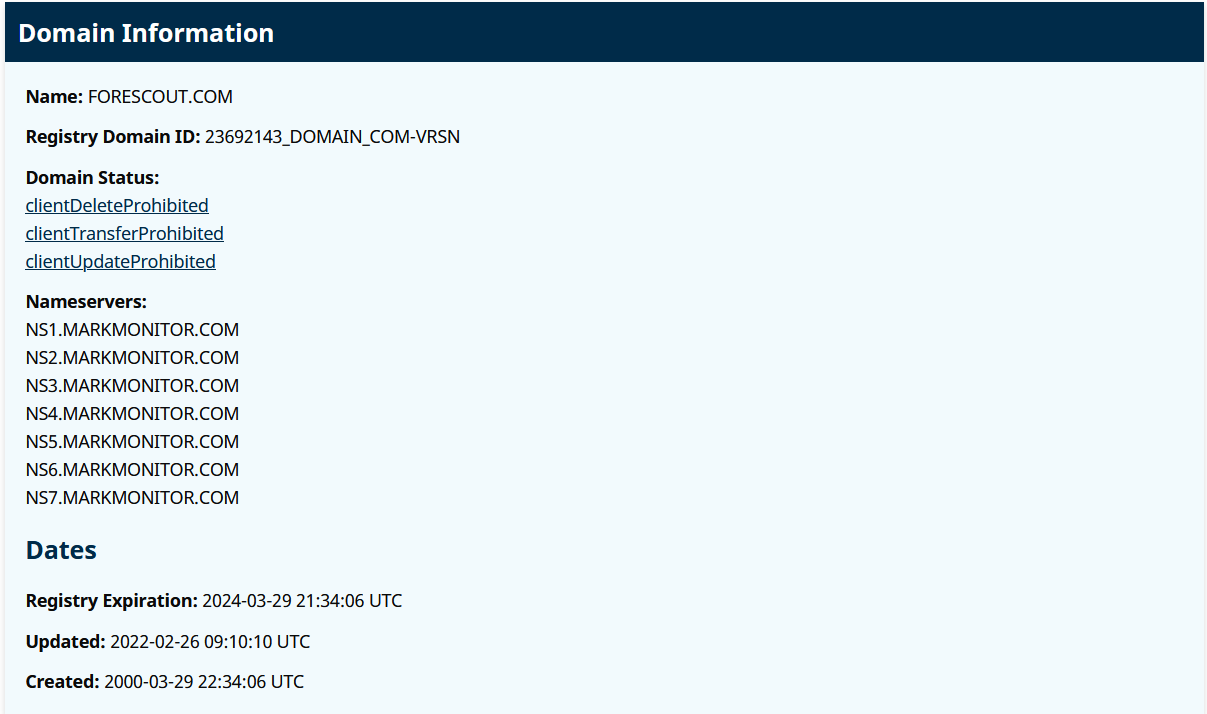
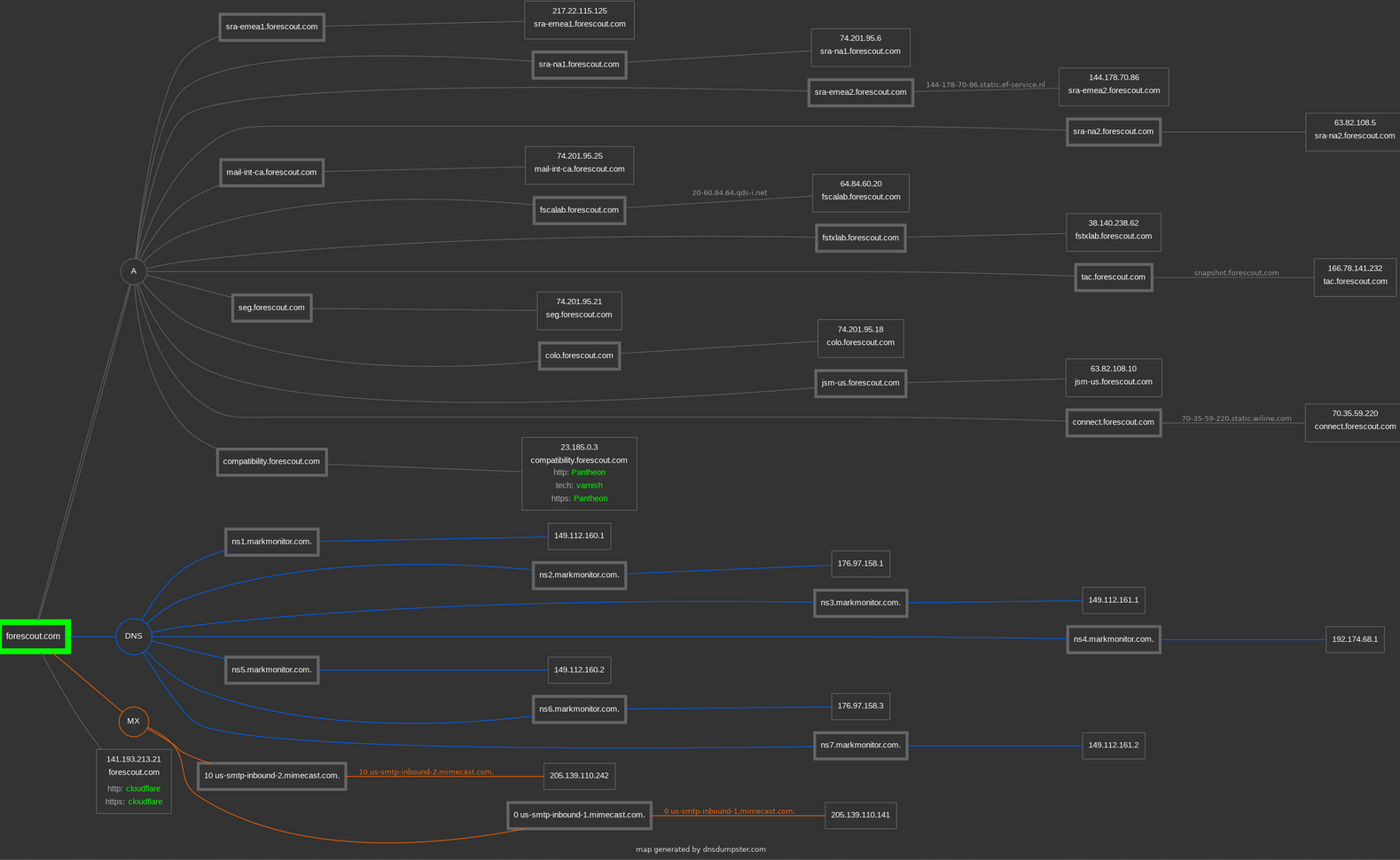
For passive subdomain enumeration, I like DNSdumpster. There are quite a few tools to take a look at subdomains, but a lot of them use active profiling.
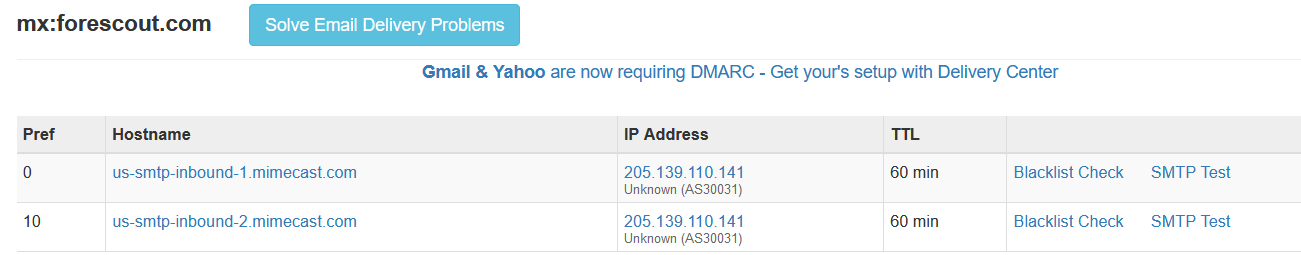
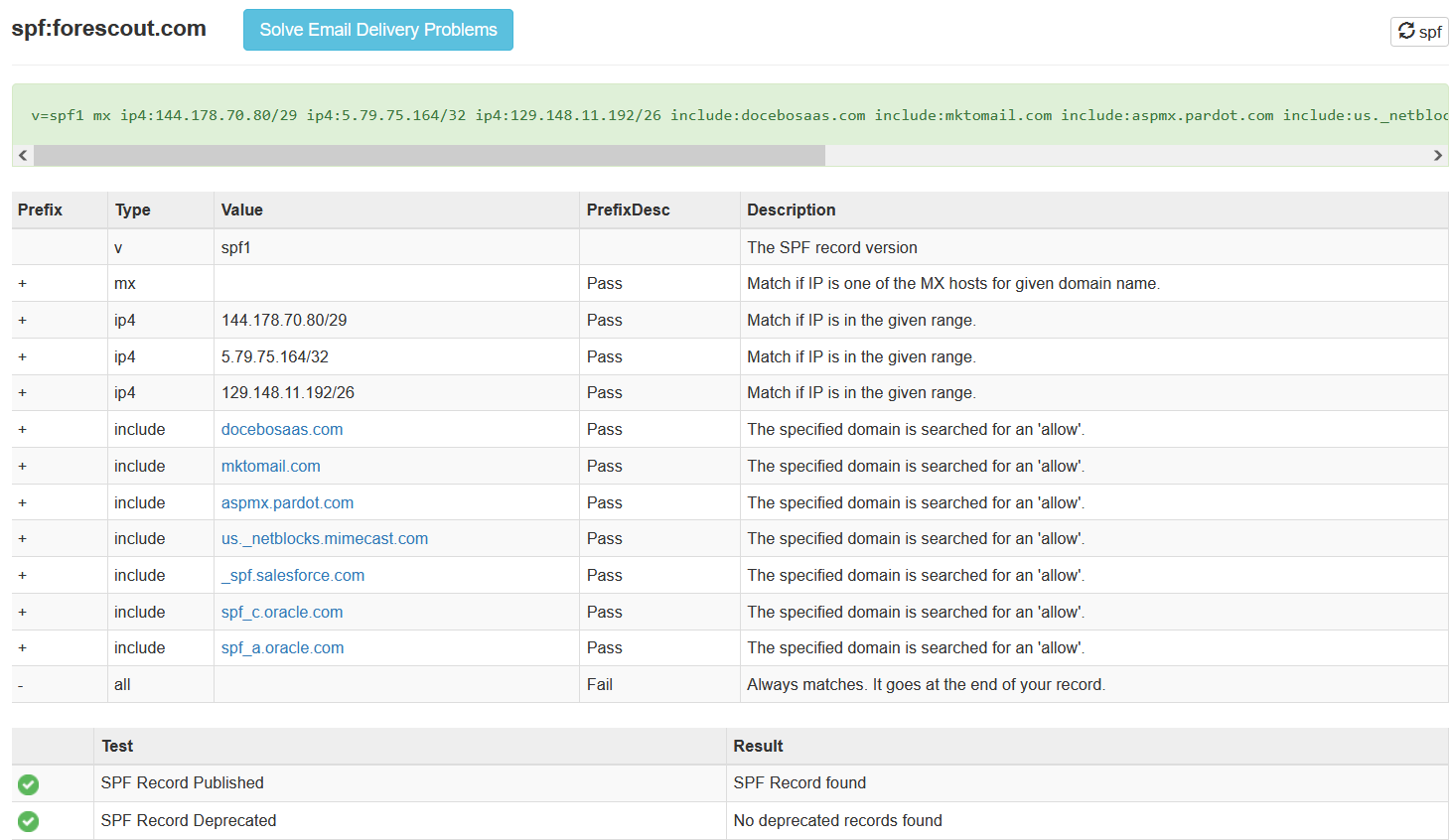
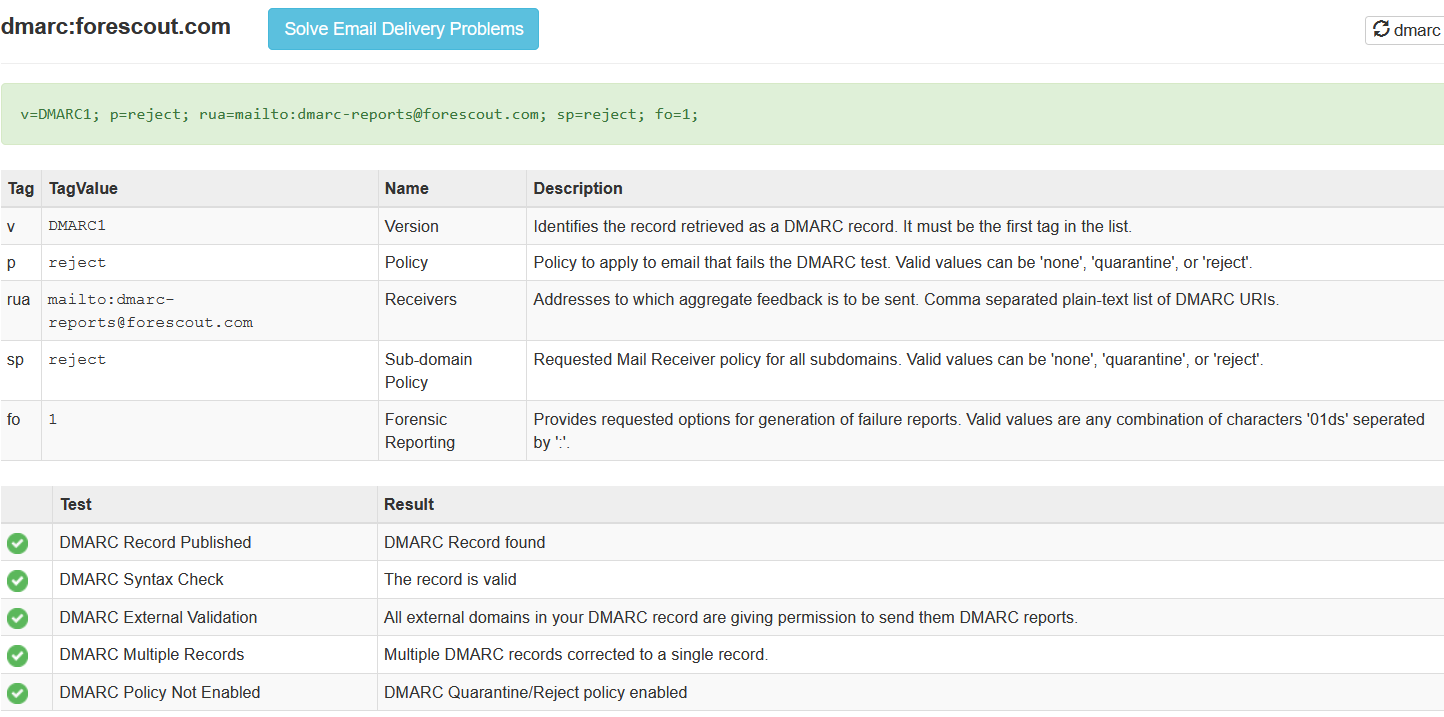
You can also use something like viewdns.info and their DNS report tool to get a barney-style report of the organizations DNS records. Speaking of DNS records, it's also a good idea to take a look at mail records.Some of this info is present on DNS dumpster, but you'll get a more comprehensive view by using MXToolbox and the MX Lookup, SPF Record Lookup, and DMARC Lookup tools.
Relevance So Far
At this point, you may be thinking 'Why does this matter? We haven't interacted with any ports or services or found any kind of exploit'. That's absolutely true, however, we now know more about the target. From the perspective of an attacker, we have enough information for an initial profile. I'm going to list some information that we now know, if you didn't catch it, go back and review the screenshots.
- The target has several ranges of IP addresses available for scanning. The larger the attack surface, the more likely a hole is present.
- Their ISP in at least one network block is Charter-Spectrum. Their domain registrar is MarkMonitor. Some threat actors may have specific methods for dealing with customers of these companies. These could also be used as part of a social engineering campaign.
- We've identified a partial technology/vendor stack - Mimecast, Oracle, Docebo SAAS, Salesforce
- We have additional IP blocks to profile from the SPF records
- We have additional attack surface from subdomains
Shodan
The first thing I'm going to check from here is what services are known to be exposed to the internet. These could be web ports, FTP servers, SMTP, cameras, RDP, or any number other things. These days, there are a handful of sites you can do this with. My primary go-to's are Shodan and FOFA.
With Shodan, occasionally you can search for the company's name and find assets that way. This isn't the case with ForeScout. So I'll start looking at network ranges by searching net: x.x.x.x/xx. Unfortunately for us, ForeScout also doesn't have anything listed on Shodan within those ranges, so I'll look at the rather large allocation for the Hyatt program.
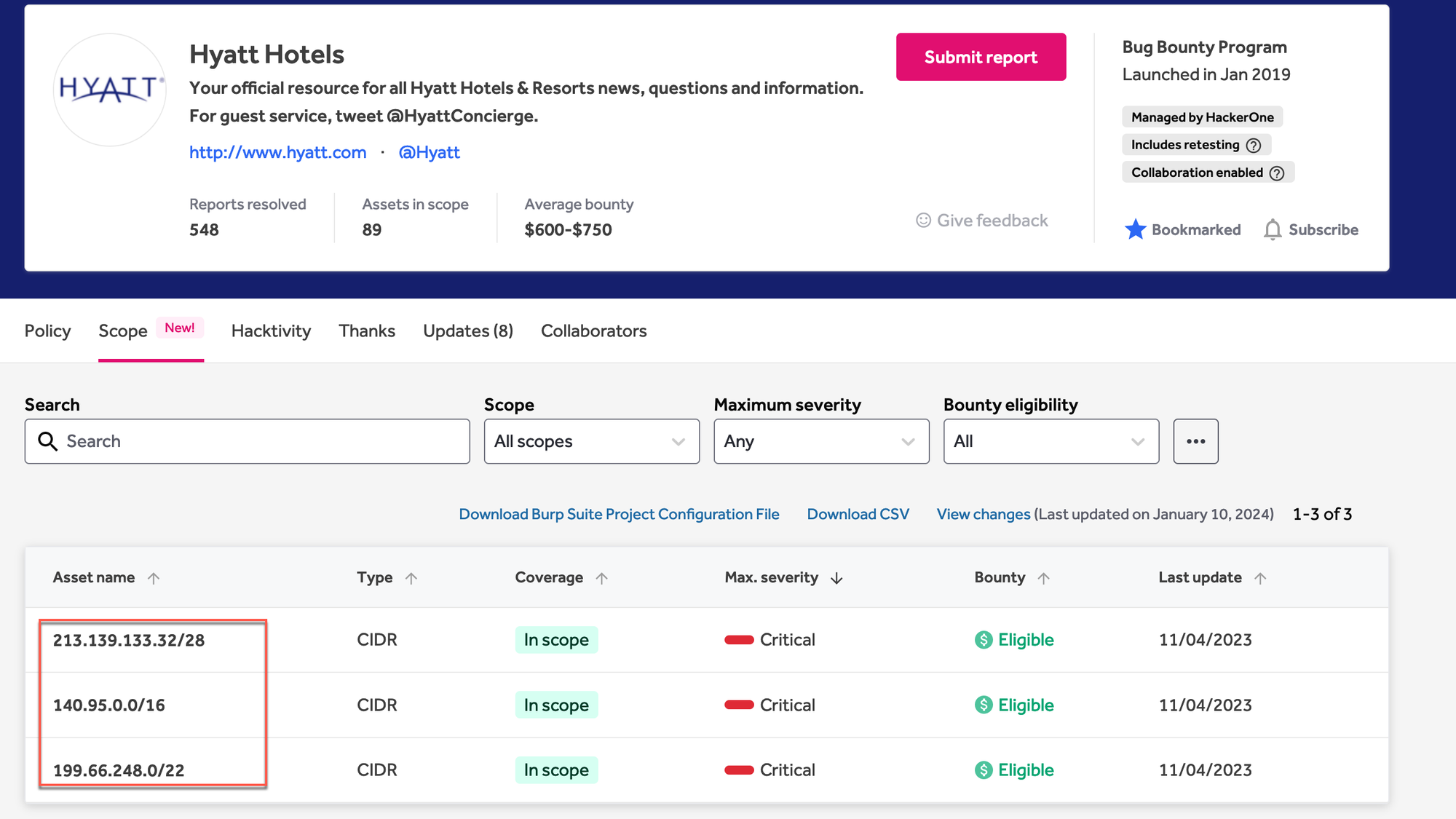
Within these ranges, there are only a handful of services that have been profiled by Shodan. Web portals on 80 and 443, as well as SNMPv3 on 161.
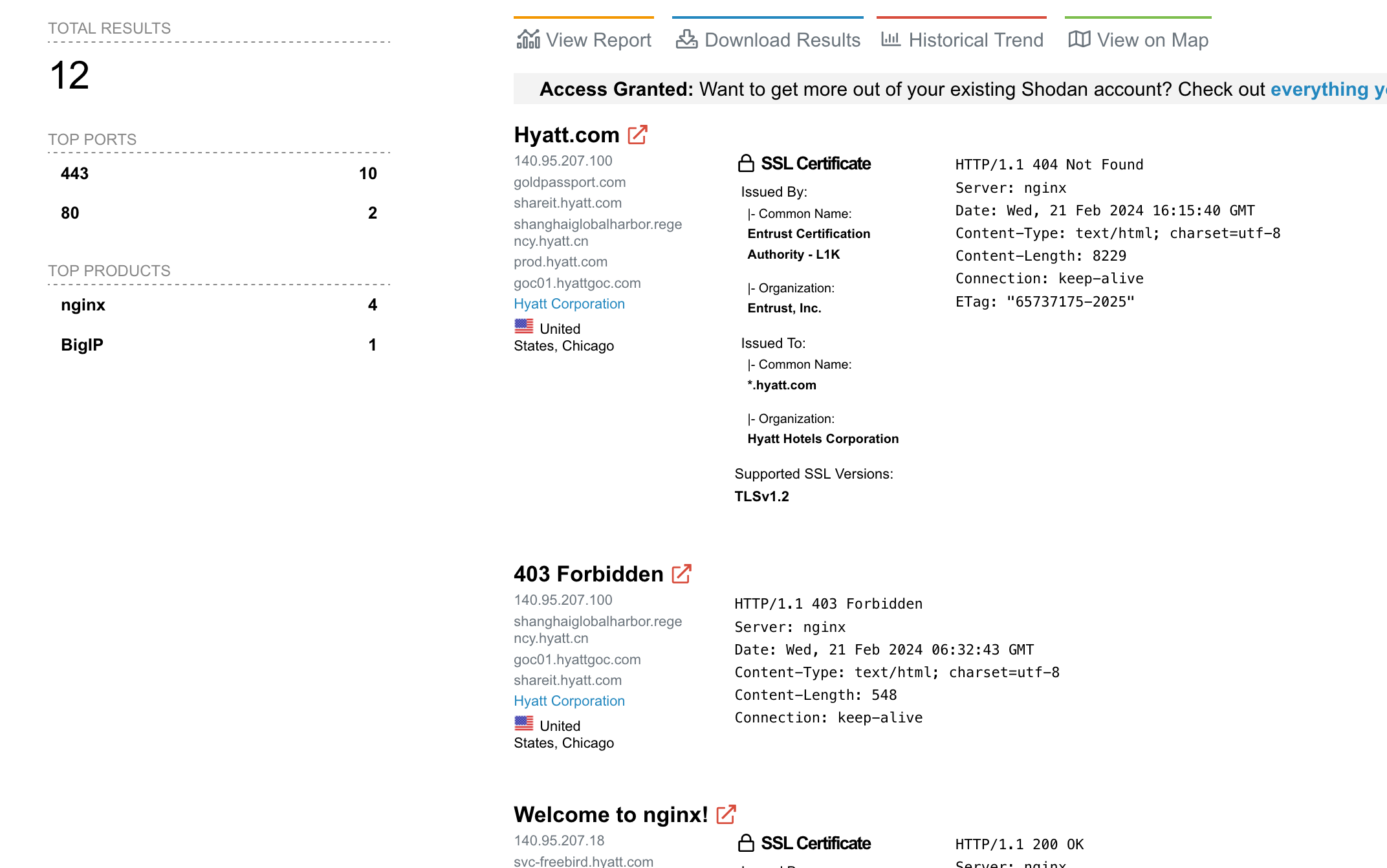
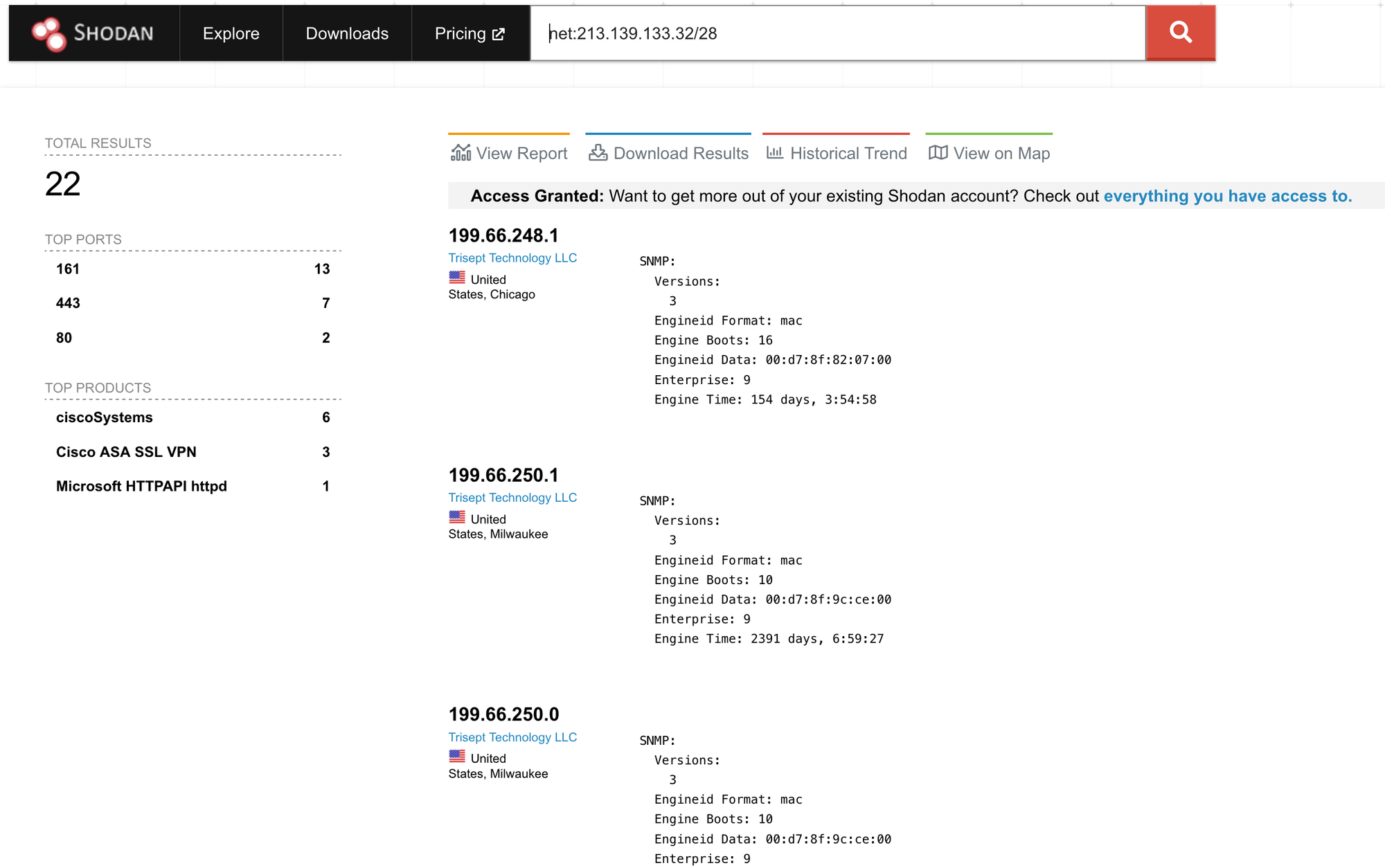
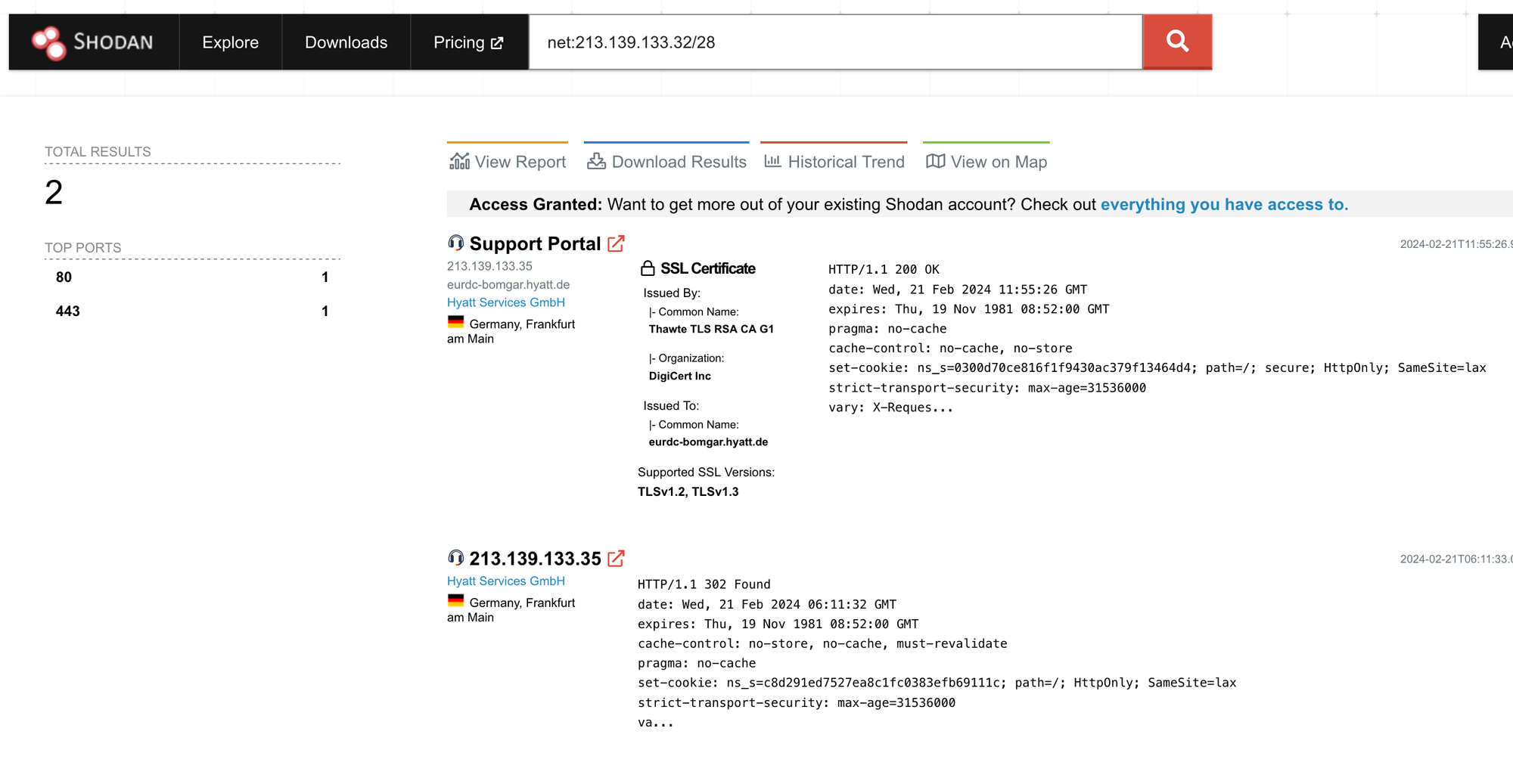
Looking through these results helps you develop a more complete technology profile. If you navigate to the results, you'll see Support Portals, Nginx web servers, Cisco VPNs and more. In cases where you get a large amount of results, you can download a report of these results or use the Shodan API to pull it all down. As of right now, you can also use the Shodan extension to get a port profile on any sites you visit.
More Tech
It's a good idea to visit any web page you identify and profile the tech used on the page, and see what else you can glean from there. Did the target build the site with a common tech stack, or are they using a CMS? What are the components and dependencies of the site? Do they have vulnerable JavaScript running with readily available PoC (Proof of Concept) exploits? Check the page source, see if there are any useful comments left behind. See if there are any links hidden in page. I like to use the Wappalyzer browser extension to get a quick profile.
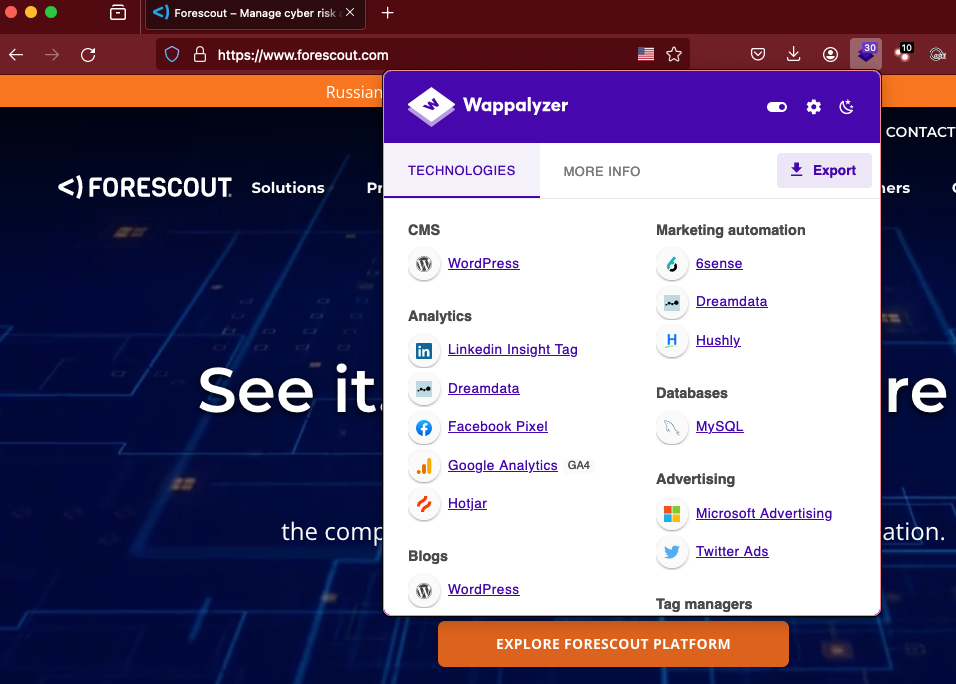
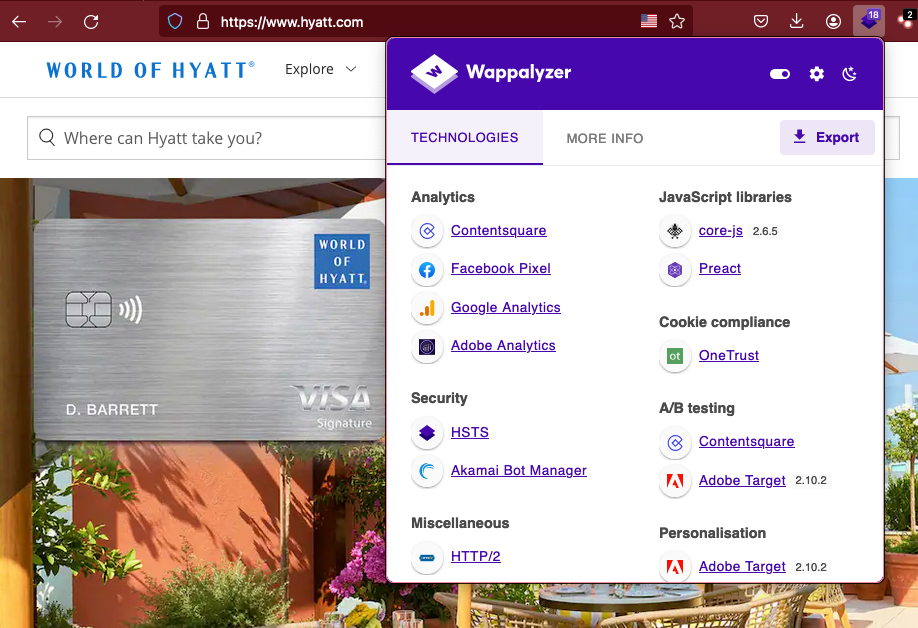
When a site uses a CMS to host their content, that opens a new avenue of exploration. What core are they using? Are there any vulnerable themes or plugins in use? Do they have appropriate permissions set on the CMS API? One of the things that I check first on any WordPress installation is the presence of a user list at /wp-json/wp/v2/users. In the case of ForeScout, they have this restricted from anonymous users. However, during the enumeration phase of a pentest, we need to keep this CMS in mind, we can scan it WPScan or manually look for common WordPress issues.
Wrapping Up
So far we've gathered quite a bit of information against our targets. This ranges across multiple attack vectors - social engineering, network attacks, and web application attacks. But there's still more information to go and get before we should even plan any attacks. I'll cover some of this in the next post. For now, thanks for reading!