Welcome back! In the previous post, we started taking a look at all of the information you can glean from a companies perimeter network and assets. In this post, we'll wrap this up and if you've followed along, you'll have an excellent foundation to do your own reconnaissance.
Emails
Among the information you gather as part of your reconnaissance activities, emails can be the cornerstone of an engagement. If you're just doing a penetration test, you can use this for password spraying. If you're performing a red team engagement or adversary simulation, you can perform phishing, credential stuffing, and lots more.
My go-to approach for emails is typically the same for all clients, I start with hunter.io. This is a paid service that typically contains an accurate list of emails for a given domain. The service will also do some basic analysis, showing how confident they are that it's a legitimate email, reporting the common username format, providing where they sourced the email, and whether or not the mail server accepts all addresses or only those that are valid (which allows for enumeration).
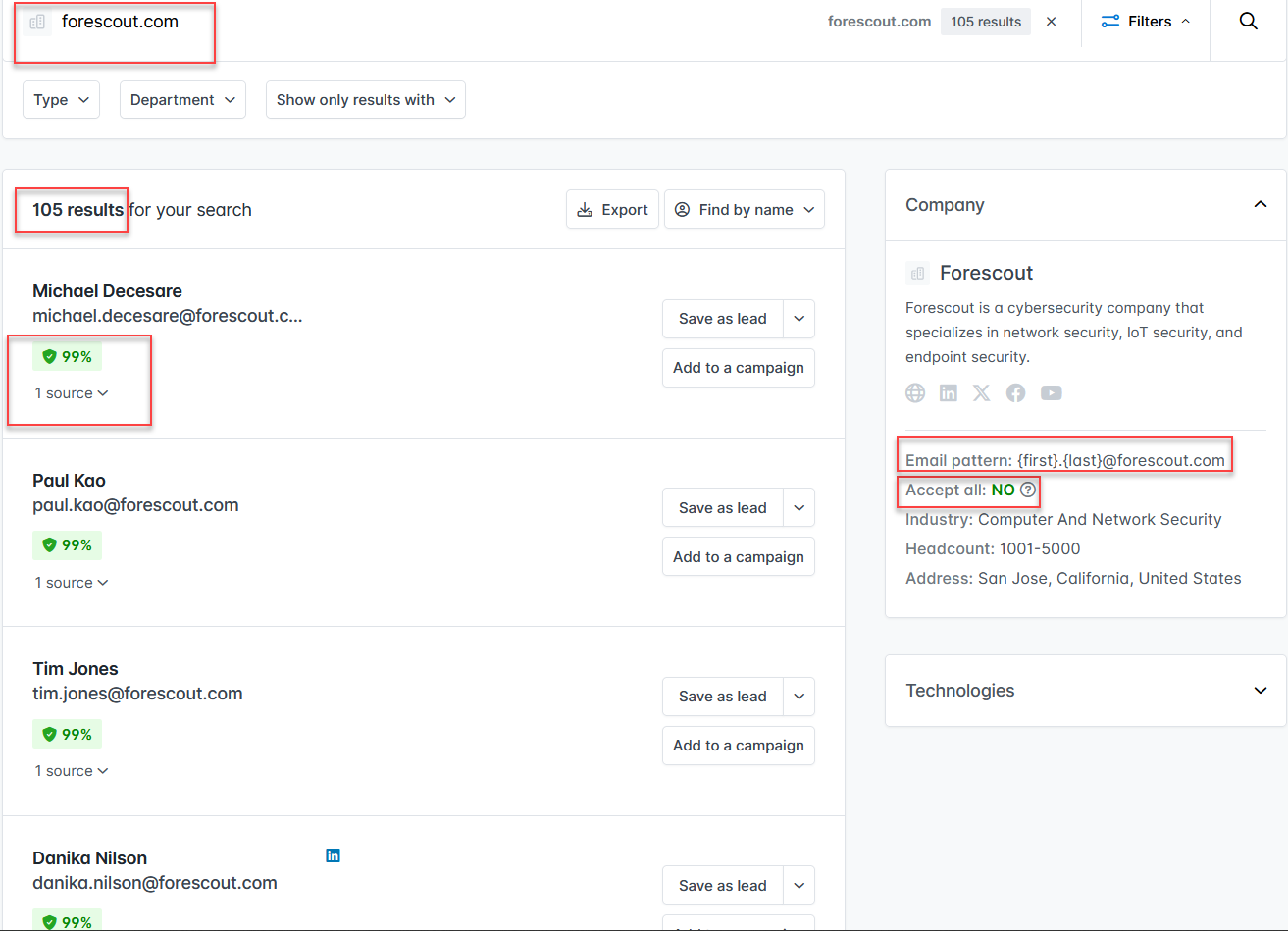
Now if you notice, that's 105 results. Hunter does have an option there for you to export, and you can use that, however I prefer leveraging the API. I wrote a tool, HunterScrape, for exactly this. It's a python script that pulls down emails listed on hunter.io. There are some limitations to the script which I discuss in the README, but I have a plan to fix that (when I get the time).
Okay, so we have some emails, but we could have more. Once I've identified highly-likely email addresses, I'll turn to LinkedIn to populate my list even further. You'll want to merge this information with your existing list and then do a `sort -u` to be sure there aren't any duplicates. Depending on the engagement, I may scour breach data brokers such as Dehashed, intelx, or BreachDirectory. This may have not only additional emails but also passwords and other sensitive information. From here, if I'm really taking a true adversary approach, I'll browse certain forums, such as BreachForums, to see if there is any relevant information. This is good for the client for two reasons: you take a more real-world approach, and if any relevant data is available you can report it to them.
Numbers
Another vital piece of information to collect when performing OSINT on an organization is a list of phone numbers. I will typically collect everything that's readily available on the company's website and google results. Beyond that, I'll use platforms such as Rocketreach and Zoominfo to collect numbers of specific individuals if I don't have that yet.
If you're targeting a higher ed institution, this should be pretty easy. As I've mentioned here, these organizations typically lay it all out for you. Other organizations may only list a support number on their page, with a receptionist number on google.
Let's Get Physical
Now we can start looking at the actual locations of the company. If googling the organization doesn't yield an address, their "Locations" or "Contact Us" pages on the primary website will usually yield something. You could also look at business records if you're desperate.
Once you have an address, start taking note of everything you can. Here are a few key considerations:
- Entrances/exits, which are public, which are employee only
- Is this a multi-tenant facility
- Foot-traffic choke points
- Loading bays
- Number of, type, and positioning of cameras
- Badge readers
Final Thoughts
Now you should have everything you need to formulate an attack regardless of the type of engagement you're performing. Perhaps in upcoming posts I can discuss leveraging this information.
I'm sorry this post took so long to come out! I was studying for the GPYC. I passed. Anyways, thanks for reading!